Friday, June 30, 2006
Microsoft Reissues Anti-Piracy Tool
Microsoft this week reissued a software component designed to detect pirated versions of Windows. Some notable technology bloggers have posted that Microsoft is preparing to push out a digital "kill switch" that could work with WGA to remotely disable machines found to be running pirated copies of Windows.
Read the article HERE.
Read the article HERE.
Spammers Using Images To Fool Filters
Earlier this year, tools began circulating among spammers to automatically vary images ever so slightly - a change in color here, a slightly larger border there. That changes the signature, helping it escape detection.
Read the article HERE.
Read the article HERE.
Maybe Firefox doesn't have the security edge
A couple of months ago, Mike Danseglio, the Program Manager for the Security Solutions group at Microsoft blamed users for the Windows security nightmare, saying "there really is no patch for human stupidity."
Nice one, Mike.
Actually, Mike, there really is no patch for that kind of blame shifting. We make software and it's our job to make it work. Designing and building software is an extremely complex process but it is not magic and it is not only possible to make it safe, it's a requirement.
Read the rest HERE.
Nice one, Mike.
Actually, Mike, there really is no patch for that kind of blame shifting. We make software and it's our job to make it work. Designing and building software is an extremely complex process but it is not magic and it is not only possible to make it safe, it's a requirement.
Read the rest HERE.
Thursday, June 29, 2006
New Laptop Security Guidelines
The Bush administration is giving federal civilian agencies 45 days to implement new measures to protect the security of personal information that agencies hold on millions of employees and citizens.
The new security guidelines, issued Friday by the White House Office of Management and Budget, cap a month marked by data thefts or disclosures at five different agencies that compromised Social Security numbers and other private data on millions of people.
Read the article HERE.
A Chronology of Data Breaches
The data breaches noted have been reported because the personal information compromised includes data elements useful to identity thieves, such as Social Security numbers, account numbers, and driver's license numbers.
View this appalling record HERE.
The new security guidelines, issued Friday by the White House Office of Management and Budget, cap a month marked by data thefts or disclosures at five different agencies that compromised Social Security numbers and other private data on millions of people.
Read the article HERE.
A Chronology of Data Breaches
The data breaches noted have been reported because the personal information compromised includes data elements useful to identity thieves, such as Social Security numbers, account numbers, and driver's license numbers.
View this appalling record HERE.
MS fixes phone home nagware
Microsoft has patched a controversial nagware update that "phoned home" every time Windows started.
Read the story HERE.
Redmond has also issued an advisory with instructions on how to remove the software.
Important : These instructions have not been tested on the general release version of the WGA Notifications. Therefore, these instructions are not supported.
Microsoft advisory HERE.
Read the story HERE.
Redmond has also issued an advisory with instructions on how to remove the software.
Important : These instructions have not been tested on the general release version of the WGA Notifications. Therefore, these instructions are not supported.
Microsoft advisory HERE.
Wednesday, June 28, 2006
20 Security Risks
The 10 Biggest Security Risks
Hackers, scammers, and identity thieves are constantly coming up with new ways to attack your PC and your privacy.
I always patch my system and run regular scans with updated antivirus and antispyware scanners. But while researching this story, I got hit by a Trojan horse (Trojan.Winloginhook.Delf.A) that was too new for my antivirus program to catch. Whether it's a new variant on a familiar foe, like a Trojan horse, or a completely new type of attack, today's threats can leave even the most security conscious among us vulnerable.
Here are the newest perils - and how to foil them.
Visit the website HERE.
The Ten Most Critical Wireless Security Vulnerabilities
Inspired by the SANS Top 20, this list is a consensus of industry experts on wireless and mobile vulnerabilities that require immediate remediation. It is offered as a public service by the Mobile Antivirus Researcher’s Association.
Read the article HERE.
Hackers, scammers, and identity thieves are constantly coming up with new ways to attack your PC and your privacy.
I always patch my system and run regular scans with updated antivirus and antispyware scanners. But while researching this story, I got hit by a Trojan horse (Trojan.Winloginhook.Delf.A) that was too new for my antivirus program to catch. Whether it's a new variant on a familiar foe, like a Trojan horse, or a completely new type of attack, today's threats can leave even the most security conscious among us vulnerable.
Here are the newest perils - and how to foil them.
Visit the website HERE.
The Ten Most Critical Wireless Security Vulnerabilities
Inspired by the SANS Top 20, this list is a consensus of industry experts on wireless and mobile vulnerabilities that require immediate remediation. It is offered as a public service by the Mobile Antivirus Researcher’s Association.
Read the article HERE.
Now it's the news that's being spammed
In this blog I try to bring you the latest security news, warning and bulletins. So imagine my surprise when a story doing the rounds today is 5 months old. The story does have genuine [ corporate ] relevence, but hawking it as a current news item is deceptive. It is a press release promoting security software.
Original Item
Slurp Audit Exposes Threat Of Portable Storage Devices For Corporate Data Theft
Arlington, VA - January 25, 2006 - Sharp Ideas, LLC, an information technology consultancy that specializes in testing and creating cost-effective IT security solutions, today announced the release of Slurp Audit - a second generation proof-of-concept application designed to demonstrate how easy it is to steal corporate data with portable storage devices (such as iPods, PDAs and USB Sticks). The application was designed to raise awareness within the corporate community about the risks associated with unmanaged portable storage devices in the workplace.
Follow Up Press Release
Centennial and Slurp.exe author team to thwart iPod threat
Thursday, 16 February 2006
Security vendor, Centennial Software, has teamed up with the author of virus-style program, Slurp.exe, to demonstrate the ease of stealing corporate data via portable devices such as USB sticks and iPods.
News Providers carrying this item as a NEW story this week
SecurityFocus - 25th June
The Register - 27th June
ITObserver - 27th June
There are many more, as well as hundreds of blogs.
It seems that even our news is now being spammed !!!
Original Item
Slurp Audit Exposes Threat Of Portable Storage Devices For Corporate Data Theft
Arlington, VA - January 25, 2006 - Sharp Ideas, LLC, an information technology consultancy that specializes in testing and creating cost-effective IT security solutions, today announced the release of Slurp Audit - a second generation proof-of-concept application designed to demonstrate how easy it is to steal corporate data with portable storage devices (such as iPods, PDAs and USB Sticks). The application was designed to raise awareness within the corporate community about the risks associated with unmanaged portable storage devices in the workplace.
Follow Up Press Release
Centennial and Slurp.exe author team to thwart iPod threat
Thursday, 16 February 2006
Security vendor, Centennial Software, has teamed up with the author of virus-style program, Slurp.exe, to demonstrate the ease of stealing corporate data via portable devices such as USB sticks and iPods.
News Providers carrying this item as a NEW story this week
SecurityFocus - 25th June
The Register - 27th June
ITObserver - 27th June
There are many more, as well as hundreds of blogs.
It seems that even our news is now being spammed !!!
Tuesday, June 27, 2006
Why home firewall software is a leaky dike
A chain is only as strong as its weakest link. That's doubly true when it comes to protecting computers that are connected to the internet. Anyone who thinks that a virtual firewall is enough to protect a PC from the dangers of the internet -- such as hacker attacks and unwanted contact with damaging programs -- is making a mistake.
The so-called personal firewall programs commonly used with home PCs are not comparable to the powerful firewalls used in companies or public organisations.
A recent test in the Munich-based computer magazine PC Professionell showed that the software often causes more problems than it solves. Not one of the six firewall programs the magazine tested, regardless of whether commercial or freeware, could prevent all attempts from the test programs at establishing outgoing connections between the PC and the internet.
Read the article HERE.
Build your own gateway firewall
Learn how to build your own gateway firewall using FreeBSD and old PC parts. The cost of this project should be between US$0 and US$200 depending on your resourcefulness.
Read the instuctions HERE.
Or, you may like to have a look at another of my favourites - IPCOP.
IPCop installation generally runs 25 minutes, and you can complete it with relatively modest hardware requirements. This document describes how to install the IPCop firewall and create a small home or office network.
Full set up details HERE.
The so-called personal firewall programs commonly used with home PCs are not comparable to the powerful firewalls used in companies or public organisations.
A recent test in the Munich-based computer magazine PC Professionell showed that the software often causes more problems than it solves. Not one of the six firewall programs the magazine tested, regardless of whether commercial or freeware, could prevent all attempts from the test programs at establishing outgoing connections between the PC and the internet.
Read the article HERE.
Build your own gateway firewall
Learn how to build your own gateway firewall using FreeBSD and old PC parts. The cost of this project should be between US$0 and US$200 depending on your resourcefulness.
Read the instuctions HERE.
Or, you may like to have a look at another of my favourites - IPCOP.
IPCop installation generally runs 25 minutes, and you can complete it with relatively modest hardware requirements. This document describes how to install the IPCop firewall and create a small home or office network.
Full set up details HERE.
Monday, June 26, 2006
Identity thieves lurking in P2P networks
Users of peer-to-peer file-sharing services may be sharing more than they bargained for. Medical records, financial information and router passwords have all popped up on P2P networks, often after users inadvertently share folders containing the data.
Hackers have already evolved sophisticated techniques for using Google Inc.'s search engine to unearth data that has accidentally been exposed on Web sites. But with P2P data mining, attackers can get access to data on a victim's desktop.
"You can set something up for an hour, search for it, and you're gone," Schmidt said. He estimates that there are nearly four times as many P2P searches conducted each day as there are Google searches.
Read the article HERE.
Hackers have already evolved sophisticated techniques for using Google Inc.'s search engine to unearth data that has accidentally been exposed on Web sites. But with P2P data mining, attackers can get access to data on a victim's desktop.
"You can set something up for an hour, search for it, and you're gone," Schmidt said. He estimates that there are nearly four times as many P2P searches conducted each day as there are Google searches.
Read the article HERE.
Is this your new OS ?
Ever thrown your hands in the air, cursed Microsoft, and promised yourself that you would explore the alternatives. Now you have that opportunity, by taking a "test drive" of various other operating systems at OSVids. There you can view videos of a variety of OS's from Vista to SuSe10.
Visit the OSVids website HERE.
[ Use the 1 2 3 in the top left corner to navigate ]
OpenSUSE 10.1
The easiest software to learn is always the one you already know. That's 9o% of the problem for anyone switching from any O/S to any other O/S. And of course, that's why people get so religious about them. I think the best way to cope with this is to start by acknowledging that what works for you will be different than what works for someone else.
BUT, for rich, reliable and secure home computing, there's no better choice than SUSE Linux 10.1. It features an easy-to-install Linux operating system that lets you browse the Web, send e-mail, chat with friends, organize digital photos, play movies and songs, and create documents and spreadsheets. The installation disk recognises Windows XP, formats its own space, instals itself, and then offers a dual boot capbility. AND, you need never again be afraid of visiting ANY website, with the knowledge that you are using a secure system.
Visit the SUSE Linux 10 website HERE.
Visit the OSVids website HERE.
[ Use the 1 2 3 in the top left corner to navigate ]
OpenSUSE 10.1
The easiest software to learn is always the one you already know. That's 9o% of the problem for anyone switching from any O/S to any other O/S. And of course, that's why people get so religious about them. I think the best way to cope with this is to start by acknowledging that what works for you will be different than what works for someone else.
BUT, for rich, reliable and secure home computing, there's no better choice than SUSE Linux 10.1. It features an easy-to-install Linux operating system that lets you browse the Web, send e-mail, chat with friends, organize digital photos, play movies and songs, and create documents and spreadsheets. The installation disk recognises Windows XP, formats its own space, instals itself, and then offers a dual boot capbility. AND, you need never again be afraid of visiting ANY website, with the knowledge that you are using a secure system.
Visit the SUSE Linux 10 website HERE.
Sunday, June 25, 2006
Rootkits - A new wave of invisible malware
Lately there has been a lot of discussion about rootkits and the type of threats they present. This article aims to provide a basic explanation of rootkits and how this low level technology can be used by malware developers to infiltrate computers in a way that is very difficult to detect and remove.
Read the article HERE.
More Dangerous Rootkits May Lurk On Horizon
Rootkits aren't inherently evil. But malcontents are getting better at using them, and rootkits are getting harder to detect. As the argument rages over whether rootkits can serve a useful purpose, new types of rootkits are emerging that require new methods of detecting and removing them. Rootkits hide processes, files, and network connections and can be written to perform like a device driver on any operating system.
Read the article HERE.
New Rootkit Detectors
Only a few rootkit-detection tools have received attention: the free RootkitRevealer from sysinternals.com, and F-Secure's ( BlackLight--freeware until September 1). But luckily for us, developers are working on a number of powerful, no-cost tools to detect rootkits.
Read about the others HERE.
Read the article HERE.
More Dangerous Rootkits May Lurk On Horizon
Rootkits aren't inherently evil. But malcontents are getting better at using them, and rootkits are getting harder to detect. As the argument rages over whether rootkits can serve a useful purpose, new types of rootkits are emerging that require new methods of detecting and removing them. Rootkits hide processes, files, and network connections and can be written to perform like a device driver on any operating system.
Read the article HERE.
New Rootkit Detectors
Only a few rootkit-detection tools have received attention: the free RootkitRevealer from sysinternals.com, and F-Secure's ( BlackLight--freeware until September 1). But luckily for us, developers are working on a number of powerful, no-cost tools to detect rootkits.
Read about the others HERE.
To Catch a Thief
In June 2005, I was the victim of identity theft and credit card fraud that put my world into a tizzy for quite some time.
Unless this has happened to you, you just can't imagine what a headache it can be with all the steps you have to take to clear up the mess. Perhaps you have been a victim of fraud or undoubtedly you know of someone who has experienced it. Certainly the internet has opened up this "opportunity" of victimization to more people.
Read Julies amazing story HERE.
Unless this has happened to you, you just can't imagine what a headache it can be with all the steps you have to take to clear up the mess. Perhaps you have been a victim of fraud or undoubtedly you know of someone who has experienced it. Certainly the internet has opened up this "opportunity" of victimization to more people.
Read Julies amazing story HERE.
Saturday, June 24, 2006
Security Of Messages In Outlook Express
Outlook Express includes several tools that protect the unauthorized users from accessing the electronic data, thereby increasing the privacy and integrity of the e-mail messages. The tools provided by Outlook Express allow a user to send and receive secure e-mail more securely and control the potentially unsafe e-mail messages through security zones.
Read the article HERE.
Read the article HERE.
And The Lord Said, Let There Be Spyware
"Thou shalt not distribute spyware" is not one of the Ten Commandments.
Watchers of right-wing Christian groups in the States say a new apocalyptic videogame released by cultish Revelations-based fiction series Left Behind is riddled with spyware.
Developers have incorporated software from an Israeli firm called Double Fusion. It incorporates video advertising and product placement into the game, and reportedly records players' behaviour, location, and other data to be uploaded to Left Behind's Bible-powered marketing machine.
Read this very informative article HERE.
Watchers of right-wing Christian groups in the States say a new apocalyptic videogame released by cultish Revelations-based fiction series Left Behind is riddled with spyware.
Developers have incorporated software from an Israeli firm called Double Fusion. It incorporates video advertising and product placement into the game, and reportedly records players' behaviour, location, and other data to be uploaded to Left Behind's Bible-powered marketing machine.
Read this very informative article HERE.
Friday, June 23, 2006
Utility Nukes Windows Genuine Advantage Callbacks
A private security company has found a way to nuke the controversial callback component in Microsoft's Windows Genuine Advantage anti-piracy tool.
Firewall Leak Tester, a company that provides tools to test the quality of personal firewall software, has released a utility called RemoveWGA that blocks Microsoft from "phoning home" from Windows PCs on a daily basis.
Read the article HERE.
Firewall Leak Tester, a company that provides tools to test the quality of personal firewall software, has released a utility called RemoveWGA that blocks Microsoft from "phoning home" from Windows PCs on a daily basis.
Read the article HERE.
Top 100 Network Security Tools
After the tremendously successful 2000 and 2003 security tools surveys, Insecure.Org is delighted to release this 2006 survey. I asked users from the nmap-hackers mailing list to share their favorite tools, and 3,243 people responded. This allowed me to expand the list to 100 tools, and even subdivide them into categories. Anyone in the security field would be well advised to go over the list and investigate tools they are unfamiliar with. I discovered several powerful new tools this way.
Respondents were allowed to list open source or commercial tools on any platform. Commercial tools are noted as such in the list below. No votes for the Nmap Security Scanner were counted because the survey was taken on a Nmap mailing list. This audience also means that the list is slightly biased toward “attack” tools rather than defensive ones.
You can see the list HERE.
Open-Source Security Tools a Double-Edged Sword
Open-source tools are an economical way to test the security of your network, but they're readily available to both users and attackers alike. Our guide will help ensure you don't get burnt when would-be intruders try turning them on you.
Read the article HERE.
Respondents were allowed to list open source or commercial tools on any platform. Commercial tools are noted as such in the list below. No votes for the Nmap Security Scanner were counted because the survey was taken on a Nmap mailing list. This audience also means that the list is slightly biased toward “attack” tools rather than defensive ones.
You can see the list HERE.
Open-Source Security Tools a Double-Edged Sword
Open-source tools are an economical way to test the security of your network, but they're readily available to both users and attackers alike. Our guide will help ensure you don't get burnt when would-be intruders try turning them on you.
Read the article HERE.
Microsoft exposed to second zero-day vulnerability
According to media reports a second vulnerability in Microsoft Excel has appeared on the internet. Just last week, Microsoft released a record 12 fixes (eight of which were critical), and it is currently working to resolve a separate bug targeted at Excel.
Last week a 0-day exploit was discovered that affects Microsoft Excel. The vulnerability could allow the execution of arbitrary code on an affected computer.
The term "0-day" refers to the fact that there is currently no patch available to correct the vulnerability.
However, Microsoft published a security advisory that offers workarounds to help prevent successful exploitation.
Microsoft said that the problem affects Excel 2003, and Excel Viewer 2003, Excel 2002, Excel 2000, Excel 2004 for Mac, and Excel X for Mac. The vulnerability can be exploited when Excel enters repair mode, which is typically used to repair corrupt files.
Read the article HERE.
Last week a 0-day exploit was discovered that affects Microsoft Excel. The vulnerability could allow the execution of arbitrary code on an affected computer.
The term "0-day" refers to the fact that there is currently no patch available to correct the vulnerability.
However, Microsoft published a security advisory that offers workarounds to help prevent successful exploitation.
Microsoft said that the problem affects Excel 2003, and Excel Viewer 2003, Excel 2002, Excel 2000, Excel 2004 for Mac, and Excel X for Mac. The vulnerability can be exploited when Excel enters repair mode, which is typically used to repair corrupt files.
Read the article HERE.
Thursday, June 22, 2006
World Cup Soccer Worm Disables Security Software
A vulgar new worm has been found spreading that is taking advantage of the 2006 World Cup. The worm arrives as an E-mail attachment with one of the following subjects and message bodys:
Subjects:
1. Soccer fans killed five teens
2. Crazy soccer fans
3. Please reply me Tomas
4. My tricks for you
5. Naked World Cup game set
6. My sister whores, shit i dont know
Read more about the worm HERE.
Subjects:
1. Soccer fans killed five teens
2. Crazy soccer fans
3. Please reply me Tomas
4. My tricks for you
5. Naked World Cup game set
6. My sister whores, shit i dont know
Read more about the worm HERE.
Dell laptop explodes

An INQUIRER reader attending a conference in Japan was sat just feet away from a laptop computer that suddenly exploded into flames, in what could have been a deadly accident.
For the record, this is a Dell machine. It is only a matter of time until such an incident breaks out on a plane.
Read the article HERE.
Researchers hack Wi-Fi driver to breach laptop
One of many flaws found allowed them to take over a laptop by exploiting a bug in an 802.11 wireless driver. Security researchers have found a way to seize control of a laptop computer by manipulating buggy code in the system's wireless device driver.
Read the article HERE.
Read the article HERE.
Wednesday, June 21, 2006
Windows Vista Beta
How to dual-boot Windows XP and Windows Vista
Now, Microsoft says only developers, testers and those "experienced in PC troubleshooting" should install this on a spare machine. But I'm young, stupid and reckless so I installed Vista on my main PC which is the only machine I have souped up enough to handle the Vistage. I didn't want to let go of XP, though, in case everything went to hell. Thankfully all turned out well: I now have a single dual-boot PC that can run either Vista or XP.
Read the "how to" article HERE.
Microsoft Halts Unauthorized Vista Downloads
I know many of you are having difficulty in downloading Vista. The demand has exceeded all expectations. Microsoft has forwarded a cease-and-desist order to VistaTorrent.com, asking the site's operators to stop their distribution of the latest beta test version of the Windows Vista operating system.
VistaTorrent was launched by a pair of Microsoft enthusiasts, including Chris Pirillo [founder of Lockergnome] who said he had a reputation to protect by ensuring VistaTorrent's legitimacy and security.
Read the article HERE.
But the torrent is alive and well, and out there
Windows Vista Beta 2 Public Release.torrent
http://www.mininova.org/tor/334001
Please read the comments before downloading.
And don't forget - it is a Beta
Windows Vista Beta 2 Dowload Links
• Windows Vista Beta 2, English 32-Bit Edition
• Windows Vista Beta 2, English 64-Bit Edition
Passwords
XDB43 - XW9MV - VDFHM - QJ8Q9 - K3G78
V2H7K - BBCXC - 7HCD9 - 6MX7H - J3QFQ
Have fun .............
Now, Microsoft says only developers, testers and those "experienced in PC troubleshooting" should install this on a spare machine. But I'm young, stupid and reckless so I installed Vista on my main PC which is the only machine I have souped up enough to handle the Vistage. I didn't want to let go of XP, though, in case everything went to hell. Thankfully all turned out well: I now have a single dual-boot PC that can run either Vista or XP.
Read the "how to" article HERE.
Microsoft Halts Unauthorized Vista Downloads
I know many of you are having difficulty in downloading Vista. The demand has exceeded all expectations. Microsoft has forwarded a cease-and-desist order to VistaTorrent.com, asking the site's operators to stop their distribution of the latest beta test version of the Windows Vista operating system.
VistaTorrent was launched by a pair of Microsoft enthusiasts, including Chris Pirillo [founder of Lockergnome] who said he had a reputation to protect by ensuring VistaTorrent's legitimacy and security.
Read the article HERE.
But the torrent is alive and well, and out there
Windows Vista Beta 2 Public Release.torrent
http://www.mininova.org/tor/334001
Please read the comments before downloading.
And don't forget - it is a Beta
Windows Vista Beta 2 Dowload Links
• Windows Vista Beta 2, English 32-Bit Edition
• Windows Vista Beta 2, English 64-Bit Edition
Passwords
XDB43 - XW9MV - VDFHM - QJ8Q9 - K3G78
V2H7K - BBCXC - 7HCD9 - 6MX7H - J3QFQ
Have fun .............
Two New Products Released
GRISOFT Launches Anti-Spyware Software
GRISOFT, the maker of award-winning AVG Anti-Virus, today announced the release of ewido anti-spyware 4.0, which provides comprehensive protection against a wide array of security threats. This new version is the only anti-spyware software to include a powerful combination of advanced security features such as generic unpacking of compressed malware, true memory scanning, heuristics, and use of binary signatures for the most thorough analysis of programs that place users’ computers at risk.
Additionally, the new release provides extended analysis tools that allow users to manually inspect their computers for suspicious activities by tracking running processes, start-up entries, current Internet connections, and detection of browser plug-ins. It also supports Fast User Switching - a feature of Windows XP – that allows several users to be simultaneously logged onto a workstation without compromising security.
Ewido anti-spyware has a fully functional 30-day trial version, but there are no plans for a free version.
Read the press release HERE.
Dekart Launches Portable Password Carrier
Secure Web Form Filler And Password Manager for USB Drives
Dekart launches Dekart Password Carrier, secure web form filler and password management tool that provides one-click login to web sites from USB drives. With Password Carrier and a USB flash drive, you can plug into any Windows PC and be productivewherever you are. Password Carrier protects your online identity by providing phishing protection, keylogger protection and strong password generation.
Read the press release HERE.
GRISOFT, the maker of award-winning AVG Anti-Virus, today announced the release of ewido anti-spyware 4.0, which provides comprehensive protection against a wide array of security threats. This new version is the only anti-spyware software to include a powerful combination of advanced security features such as generic unpacking of compressed malware, true memory scanning, heuristics, and use of binary signatures for the most thorough analysis of programs that place users’ computers at risk.
Additionally, the new release provides extended analysis tools that allow users to manually inspect their computers for suspicious activities by tracking running processes, start-up entries, current Internet connections, and detection of browser plug-ins. It also supports Fast User Switching - a feature of Windows XP – that allows several users to be simultaneously logged onto a workstation without compromising security.
Ewido anti-spyware has a fully functional 30-day trial version, but there are no plans for a free version.
Read the press release HERE.
Dekart Launches Portable Password Carrier
Secure Web Form Filler And Password Manager for USB Drives
Dekart launches Dekart Password Carrier, secure web form filler and password management tool that provides one-click login to web sites from USB drives. With Password Carrier and a USB flash drive, you can plug into any Windows PC and be productivewherever you are. Password Carrier protects your online identity by providing phishing protection, keylogger protection and strong password generation.
Read the press release HERE.
Tuesday, June 20, 2006
Osama Bin Laden Dead
Did that grab your attention? It was meant to.
Neither is Osama Bin Laden dead, nor has Michael Jackson committed suicide, regardless of what some malicious spam messages will tell you. Sure this is a good way to get your attention and maybe get you to open an email, precisely the bad guys' goal.
Read the article HERE.
Yamanner: The First Of Many?
Last week, a new worm known as "Yamanner" spread through Yahoo's e-mail system. The problem was solved in short order and did relatively little damage while it still existed. What's more troubling is how the worm spread - when users opened just the e-mail itself, not any attachments, it sprang into action-and the strong possibility that more could follow suit.
Read the article HERE.
How can we avoid something like this happening to us ? EASY !!!
For many years I have using a Free Email Notification and Retrieval Programme named ePrompter. ePrompter is an easy to use email notifier that automatically checks up to sixteen password protected email accounts. It allows you to compose, forward and reply to the messages that have been retrieved for you. Your forwards and replies will be sent back through the account that the messages were retrieved from.
Learn about this excellent utility HERE.
Neither is Osama Bin Laden dead, nor has Michael Jackson committed suicide, regardless of what some malicious spam messages will tell you. Sure this is a good way to get your attention and maybe get you to open an email, precisely the bad guys' goal.
Read the article HERE.
Yamanner: The First Of Many?
Last week, a new worm known as "Yamanner" spread through Yahoo's e-mail system. The problem was solved in short order and did relatively little damage while it still existed. What's more troubling is how the worm spread - when users opened just the e-mail itself, not any attachments, it sprang into action-and the strong possibility that more could follow suit.
Read the article HERE.
How can we avoid something like this happening to us ? EASY !!!
For many years I have using a Free Email Notification and Retrieval Programme named ePrompter. ePrompter is an easy to use email notifier that automatically checks up to sixteen password protected email accounts. It allows you to compose, forward and reply to the messages that have been retrieved for you. Your forwards and replies will be sent back through the account that the messages were retrieved from.
Learn about this excellent utility HERE.
Coca-Cola lottery is not the real thing
Experts at SophosLabs have warned of an email scam that pretends to be notification of a lottery win from Coca-Cola. This scam attempts to steal money and commit identity theft.
Read the full release HERE.
This scam is a version of an advance fee fraud scam. To refresh your memory of the various types of scams roaming the Internet, click HERE.
Read the full release HERE.
This scam is a version of an advance fee fraud scam. To refresh your memory of the various types of scams roaming the Internet, click HERE.
Monday, June 19, 2006
World Blogger Championship of Online Poker
I would like to thank those people who sent me an email wishing me well at this event.
Of the 2247 entrants, I managed to finish 41st and pick up a small prize.
Many Thanks.
Of the 2247 entrants, I managed to finish 41st and pick up a small prize.
Many Thanks.
Microsoft France Defaced
First reported by SecuriTeam Blogs , Microsoft France has suffered an embarrasing hack.
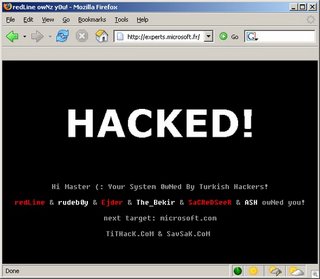
So I guess Windows Server 2003 isn’t that secure after all, even if configured by Microsoft.
Really makes you think doesn’t it.
It's just a little silly to use Microsoft and Security in the same sentence.

So I guess Windows Server 2003 isn’t that secure after all, even if configured by Microsoft.
Really makes you think doesn’t it.
It's just a little silly to use Microsoft and Security in the same sentence.
Sunday, June 18, 2006
USB flash key failures increase 300%
The increasingly popular keyring memory stick may be a good way to transfer data but as a permanent back-up device it doesn't cut the mustard, as an increasing number of people are painfully finding out, according to a data recovery specialist.
USB flash drives are increasingly the storage or back up device of choice for individuals and small businesses and with this growth there is an alarming increase in problems and disaster stories, says the boss of Australian data recovery specialist Payam Data Recovery (PDR).
Although they have been designed the be fairly durable, attaching USB flash drives to key-chains and briefcases or carelessly throwing them onto desks and into draws exposes them to constant knocks, hot temperatures and other day-to-day dangers, which the devices aren’t designed to continually handle.
Read the article HERE.
USB flash drives are increasingly the storage or back up device of choice for individuals and small businesses and with this growth there is an alarming increase in problems and disaster stories, says the boss of Australian data recovery specialist Payam Data Recovery (PDR).
Although they have been designed the be fairly durable, attaching USB flash drives to key-chains and briefcases or carelessly throwing them onto desks and into draws exposes them to constant knocks, hot temperatures and other day-to-day dangers, which the devices aren’t designed to continually handle.
Read the article HERE.
AIG reveals personal data theft
Giant insurer American International Group says personal data on 930,000 people has been stolen. A burglar stole computer equipment on March 31 [and they let us know almost 3 months later] from one of AIG's Midwest offices.
Companies have no incentives, negative or positive, to protect your data
Another in a continually growing long list of personal data losses by the corporate world. We are all being constantly urged to "secure" our computers, surf safely, and be alert to the threats around us. Yet those resposible for securing our private information - information we are forced to divulge - give little or no concern to its safety.
The headlines above are news stories you are probably familiar with.
Ernst & Young, three lost laptops in one 6 months period, so obviuosly they take security seriously. Is there a solution ?
Make the CEO responsible for data breaches
Companies have no incentives, negative or positive, to protect your data
Another in a continually growing long list of personal data losses by the corporate world. We are all being constantly urged to "secure" our computers, surf safely, and be alert to the threats around us. Yet those resposible for securing our private information - information we are forced to divulge - give little or no concern to its safety.
- Personal data on 2.2 million troops stolen
- Personal data of 26.5M veterans stolen
- Laptop theft compromises Hotels.com customer data
- Stolen Fidelity Laptop Exposes HP Workers
- Laptop theft puts data of 98,000 at risk
The headlines above are news stories you are probably familiar with.
Ernst & Young, three lost laptops in one 6 months period, so obviuosly they take security seriously. Is there a solution ?
Make the CEO responsible for data breaches
Martin McKeay, in a recent Computerworld Blog, presents some excellent ideas.
Until upper management feels a direct impact, either to the bottom line or their personal status, security breaches are going to continue.
Saturday, June 17, 2006
Hackers Aiming at Instant Messages
In typical IM attacks, hackers send out e-mail or IM programs designed to find and steal computer users' "buddy lists." Using automated computers, the hackers then will send unsolicited instant messages to everybody on that person's list, masquerading as the person and luring recipients to check out a fake Web site.
Last month, the number of instant messages containing computer "malware" soared by 500 percent from the previous month, according to one Internet security company. In the first quarter of 2006, the number was up more than 160 percent from a year earlier.
Last year, security experts found 2,400 different viruses, worms and other threats that hackers attached to instant messages, an increase of nearly 1,600 percent from the previous year. The programs were designed to take over computers, steal online passwords or break into computer files.
Read the article HERE.
New Worm Targets MSN Messenger
PandaLabs, the laboratory of the security software company Panda Software, warns of the spread of the new B variant of the BlackAngel worm. PandaLabs has apparently already received several incidents from users affected by this worm.
This worm spreads via Microsoft’s instant messaging program MSN Messenger. In order to spread through this tool, it sends messages to all the contacts in the user’s contacts list, disguising itself as a video called ‘Fantasma’ (Ghost).
Read the Panda press release HERE.
What Is Gaim?
For those that missed it, here's a reminder.
Last month, the number of instant messages containing computer "malware" soared by 500 percent from the previous month, according to one Internet security company. In the first quarter of 2006, the number was up more than 160 percent from a year earlier.
Last year, security experts found 2,400 different viruses, worms and other threats that hackers attached to instant messages, an increase of nearly 1,600 percent from the previous year. The programs were designed to take over computers, steal online passwords or break into computer files.
Read the article HERE.
New Worm Targets MSN Messenger
PandaLabs, the laboratory of the security software company Panda Software, warns of the spread of the new B variant of the BlackAngel worm. PandaLabs has apparently already received several incidents from users affected by this worm.
This worm spreads via Microsoft’s instant messaging program MSN Messenger. In order to spread through this tool, it sends messages to all the contacts in the user’s contacts list, disguising itself as a video called ‘Fantasma’ (Ghost).
Read the Panda press release HERE.
What Is Gaim?
For those that missed it, here's a reminder.
PayPal Security Flaw Allows Identity Theft
A security flaw in the PayPal web site is being actively exploited by fraudsters to steal credit card numbers and other personal information belonging to PayPal users.
The PayPal site, owned by eBay, allows users to make online payments to one another, charged to their credit cards. Login credentials for the service are a prized target of fraudsters.
Read the alert HERE.
The PayPal site, owned by eBay, allows users to make online payments to one another, charged to their credit cards. Login credentials for the service are a prized target of fraudsters.
Read the alert HERE.
Friday, June 16, 2006
The truth about Windows Genuine Advantage
Is Microsoft tracking your daily whereabouts via its anti-piracy technology? Is it collecting information on which non-Microsoft apps you are running? Here's our attempt to separate fact from urban legend in the Genuine Advantage realm.
Read the article HERE.
How MS spyware could be used by hackers to disable systems
An anonymous Slashdot user gives virus writers a worrying idea: "A virus could use one of the 'Product-Key Changer' scripts ... to install a pirated product key on every infected computer (wiping all traces of the original key). This would render millions of genuine installations indistinguishable from pirated installations. What a mess for Microsoft! They would have to immediately 'kill forever' the WGA helper, and maybe even remove the WGA check on Windows Update. Such a virus would be a hard lesson to learn for the writers of all kinds of automated 'genuine' checks."
Read the article HERE.
How MS spyware could be used by hackers to disable systems
An anonymous Slashdot user gives virus writers a worrying idea: "A virus could use one of the 'Product-Key Changer' scripts ... to install a pirated product key on every infected computer (wiping all traces of the original key). This would render millions of genuine installations indistinguishable from pirated installations. What a mess for Microsoft! They would have to immediately 'kill forever' the WGA helper, and maybe even remove the WGA check on Windows Update. Such a virus would be a hard lesson to learn for the writers of all kinds of automated 'genuine' checks."
New Adobe Version Plugs Security Holes
Adobe has released yet another update of its Adobe Reader for PDF documents that fixes several security flaws in both the Windows and Mac OS X versions.
The latest version, 7.0.8, includes several stability and security bug fixes.
Learn more HERE.
The latest version, 7.0.8, includes several stability and security bug fixes.
Learn more HERE.
Thursday, June 15, 2006
Vista goes public
Techies have been testing it for months, but until now, most of us had to wait.
NO more. You can download the "Customer Preview Edition" here.
Or, you can read about a test instal HERE.
Vista Readiness Test
Welcome to PC Pitstop's Vista Readiness Center. Windows Vista is Microsoft's highly hyped, and highly delayed operating system. In May, 2006, Microsoft finally released the hardware requirements to their new operating system due to ship in early 2007. Can your PC stack up with the mighty spec's of Windows Vista? Our Vista Readiness Test quickly analyzes your PC against the Microsoft specification.
Take the test
For any of you looking at BitTorrent, I have downloaded 2 and they both were fakes. So be careful.
NO more. You can download the "Customer Preview Edition" here.
Or, you can read about a test instal HERE.
Vista Readiness Test
Welcome to PC Pitstop's Vista Readiness Center. Windows Vista is Microsoft's highly hyped, and highly delayed operating system. In May, 2006, Microsoft finally released the hardware requirements to their new operating system due to ship in early 2007. Can your PC stack up with the mighty spec's of Windows Vista? Our Vista Readiness Test quickly analyzes your PC against the Microsoft specification.
Take the test
For any of you looking at BitTorrent, I have downloaded 2 and they both were fakes. So be careful.
More Windows Exploits
Its back to see Brian Krebs at Security Fix for more Windows exploits.
Several security sources are reporting that "exploit code" - instructions showing bad guys how to attack vulnerabilities - has been posted online for several more security flaws for which Microsoft just issued patches.
Why are we not surprised? Read more HERE.
Several security sources are reporting that "exploit code" - instructions showing bad guys how to attack vulnerabilities - has been posted online for several more security flaws for which Microsoft just issued patches.
Why are we not surprised? Read more HERE.
Wednesday, June 14, 2006
End of Support: Microsoft's Service Pack 1
On July 11, 2006 and October 10, 2006, Microsoft will end all public assisted support for Service Pack1 (SP1) (see affected products). After this date, Microsoft will no longer provide any incident support options or security updates for this retired service pack under the policies defined by the Microsoft Support Lifecycle policy.
To enhance the security of your computer and to continue to receive updates for the products, it is recommend you upgrade your computer, for free, to newer Service Pack.
See the details HERE.
To enhance the security of your computer and to continue to receive updates for the products, it is recommend you upgrade your computer, for free, to newer Service Pack.
See the details HERE.
12 Microsoft Patches Plug 21 Security Holes
Microsoft today released a dozen security updates to fix at least 21 vulnerabilities in its Windows operating system and other software, including 12 flaws Redmond labeled "critical", its most severe warning level.
As usual, we have a link to Brian Krebs expert analysis of these updates.
View the updates HERE.
As usual, we have a link to Brian Krebs expert analysis of these updates.
View the updates HERE.
Tuesday, June 13, 2006
Microsoft finds malware on 5.7M tested PCs
Microsoft Corp. is set to release research showing, among other things, that its security tools find malicious software on about one in every 311 times it scans a PC. The research is part of a major report on security trends that Microsoft plans to release today at its TechEd user conference in Boston.
Microsoft's data is remarkable because it comes from such a large sample group -- more than 270 million users of the Windows Malicious Software Removal Tool, which ships with Windows.
Between January 2005 and March 2006, that tool was used to remove 16 million pieces of malware from 5.7 million computers. The software was used to scan systems 2.7 billion times during that period, and on average, it finds something malicious about 0.32% of the time, or in one out of every 311 scans, according to Microsoft.
Read the story HERE.
Microsoft's data is remarkable because it comes from such a large sample group -- more than 270 million users of the Windows Malicious Software Removal Tool, which ships with Windows.
Between January 2005 and March 2006, that tool was used to remove 16 million pieces of malware from 5.7 million computers. The software was used to scan systems 2.7 billion times during that period, and on average, it finds something malicious about 0.32% of the time, or in one out of every 311 scans, according to Microsoft.
Read the story HERE.
Yahoo Webmail Worm on the Loose
Security experts are warning of a new e-mail worm that takes advantage of a flaw in Yahoo's Web mail system to redirect users to advertising sites and to spread the worm to everyone in the victim's e-mail address book.
SANS says it's aware of two versions of this worm going around, released just two hours apart: "The [quick] release of a new version ... which partially fixes the first version indicates that the code is very much under development and you should assume that the remaining bugs will be rapidly ironed out."
Read the article HERE.
SANS says it's aware of two versions of this worm going around, released just two hours apart: "The [quick] release of a new version ... which partially fixes the first version indicates that the code is very much under development and you should assume that the remaining bugs will be rapidly ironed out."
Read the article HERE.
Monday, June 12, 2006
The Top 5 Ways to Prevent IP Spoofing
The term "spoofing" is generally regarded as slang, but refers to the act of fooling -- that is, presenting a false truth in a credible way. There are several different types of spoofing that occur, but most relevant to networking is the Internet Protocol (IP) spoof. Most types of spoofing have a common theme: a nefarious user transmits packets with an IP address indicating that the packets are originating from another, trusted machine.
The first step in spoofing is determining the IP address of a host the intended target trusts. After that, the attacker can change the headers of packets to make it seem like the transmissions are originating from the trusted machine.
What sorts of attacks are launched through IP spoofing?
Read the article HERE.
The first step in spoofing is determining the IP address of a host the intended target trusts. After that, the attacker can change the headers of packets to make it seem like the transmissions are originating from the trusted machine.
What sorts of attacks are launched through IP spoofing?
Read the article HERE.
Is Your Data Encryption Really Secure ?
There are various types and methods of data encryption. Some of the most popular forms of data encryption include single file encryption, folder encryption, volume encryption, whole disk encryption, and of course email encryption.
The Windows XP operating system has the ability to perform file and folder encryption. There are 3rd party tools, like PGP Desktop, which can perform whole disk, logical disk, file, and e-mail encryption.
If you routinely deal with confidential or sensitive information, or if you are concerned about private information falling into someone else's hands, encryption may be the way you want to go. However, there are a few things you should be aware of so you don't have a false sense of security.
Read the article HERE.
The Windows XP operating system has the ability to perform file and folder encryption. There are 3rd party tools, like PGP Desktop, which can perform whole disk, logical disk, file, and e-mail encryption.
If you routinely deal with confidential or sensitive information, or if you are concerned about private information falling into someone else's hands, encryption may be the way you want to go. However, there are a few things you should be aware of so you don't have a false sense of security.
Read the article HERE.
Sunday, June 11, 2006
When hacking competitions go wrong [ and right ]
A hacking contest that promised $100,000 as first prize appears to have been weighted so heavily against competitors that some decided to hack the competition rather than the target server
What do you do when you enter a hacking competition only to discover that the target server is running a cut-down operating system running with almost all services switched off so that it does not resemble a "real-world situation"?
Simple. You hack the competition itself.
Read the article HERE.
Cybersecurity contests go national
It has all the makings of a B-movie plot: A corporate network targeted by hackers and a half dozen high-school students as the company's only defense.
Yet, teams of students from ten different Iowa high schools faced exactly that scenario during a single night in late May in the High School Cyber Defense Competition. The contest tasked the teenagers with building a network in the three weeks leading up to the competition with only their teachers, and mentoring volunteers from local technology firms, as their guides.
The competitions give students and professionals the opportunity to get hands-on experience responding to attacks, without serious consequences.
Read the article HERE.
What do you do when you enter a hacking competition only to discover that the target server is running a cut-down operating system running with almost all services switched off so that it does not resemble a "real-world situation"?
Simple. You hack the competition itself.
Read the article HERE.
Cybersecurity contests go national
It has all the makings of a B-movie plot: A corporate network targeted by hackers and a half dozen high-school students as the company's only defense.
Yet, teams of students from ten different Iowa high schools faced exactly that scenario during a single night in late May in the High School Cyber Defense Competition. The contest tasked the teenagers with building a network in the three weeks leading up to the competition with only their teachers, and mentoring volunteers from local technology firms, as their guides.
The competitions give students and professionals the opportunity to get hands-on experience responding to attacks, without serious consequences.
Read the article HERE.
Saturday, June 10, 2006
Essential Wireless Hacking Tools
Anyone interested in gaining a deeper knowledge of wireless security and exploiting vulnerabilities will need a good set of base tools with which to work.
Fortunately, there are an abundance of free tools available on the Internet.
This list is not meant to be comprehensive in nature but rather to provide some general guidance on recommended tools to build your toolkit.
See the list HERE.
Fortunately, there are an abundance of free tools available on the Internet.
This list is not meant to be comprehensive in nature but rather to provide some general guidance on recommended tools to build your toolkit.
See the list HERE.
Secure your email with free software
My website and blog refer mainly to Windows issues. I have recently received a few emails from Linux users asking how best to encrypt their mail. Until now I have only been able to provide a few links, but in this article, you’ll learn how to install, setup, and use the Mozilla Thunderbird email client for secure, encrypted email using GnuPG and the Enigmail Mozilla Thunderbird extension. The examples in this article are based on Ubuntu 5.10, but any GNU/Linux-based operating system can be used.
If you’re using Microsoft Windows, you can still apply the steps presented, but you’ll have to download and configure the Win32 counterparts of the software used.
Read the article HERE.
If you’re using Microsoft Windows, you can still apply the steps presented, but you’ll have to download and configure the Win32 counterparts of the software used.
Read the article HERE.
World Blogger Championship of Online Poker
And now for something completely different.
This is an exclusive FREE poker tournament open ONLY to Internet bloggers. The $37,000 worth of prizes are available to the best 54 finishers. So, if you are a blogger, and a poker player, here's a great chance for some excellent FREE prizes.

This is an exclusive FREE poker tournament open ONLY to Internet bloggers. The $37,000 worth of prizes are available to the best 54 finishers. So, if you are a blogger, and a poker player, here's a great chance for some excellent FREE prizes.

I have registered to play in the PokerStars World Blogger Championship of Online Poker!
This Online Poker Tournament is a No Limit Texas Holdem event exclusive to Bloggers.
Registration code: 2328324
Friday, June 09, 2006
Microsoft installs SPYWARE
Why does this not come as a surprise !!!
Microsoft Corp. acknowledged that it needs to better inform users that its tool for determining whether a computer is running a pirated copy of Windows also quietly checks in daily with the software maker. "It's kind of a safety switch," said David Lazar, who directs the Windows Genuine Advantage program.
Read the full story HERE.
Microsoft Corp. acknowledged that it needs to better inform users that its tool for determining whether a computer is running a pirated copy of Windows also quietly checks in daily with the software maker. "It's kind of a safety switch," said David Lazar, who directs the Windows Genuine Advantage program.
Read the full story HERE.
Rogue pharmacy poses as Google
 The newest addition to the Google family has just hit the web - the search giant's very own accredited pharmacy, selling pills at rock bottom prices.
The newest addition to the Google family has just hit the web - the search giant's very own accredited pharmacy, selling pills at rock bottom prices.Google celebrated the launch with a brand-spanking, stylised logo - the double 'O' replaced with two blue Viagra pills. The mail promoting the new site told us: "We've just launched a pharmaceutical interfaces for Google, as well as several new features for the people buying pills and using pharmaceutical interfaces".
But, it wasn't Google, but rogue pharmaceutical site ED Choice.
Read the story HERE.
Thursday, June 08, 2006
Why Web 2.0 will end your privacy
We all know the plushy, rounded, pastel-coloured faces of Web 2.0. - MySpace. Digg. Flickr. The achingly trendy Silicon Valley startups that are selling for millions to big media conglomerates and making their founders into stars. Tom Anderson. Kevin Rose. These are the pinups of the Web 2.0 generation - but little do they know the monster they've created.
My firm belief is that the net effect of the Web 2.0 movement will be a marked loss of privacy on the internet, one which leads to big business knowing more about you than it ever did before.
This is why. Read the article HERE.
My firm belief is that the net effect of the Web 2.0 movement will be a marked loss of privacy on the internet, one which leads to big business knowing more about you than it ever did before.
This is why. Read the article HERE.
Steganos Launches Free Encryption Tool
By pasting text into a website form and entering a password, users can encrypt and decrypt messages using strong encryption, wherever they are without installing any software or paying any fees.
Users visit www.steganos.com/freecrypt where there is a form into which they can type or paste text. They enter a password and click the button and their text is quickly encrypted and displayed in another form field. From there, it can be copied for pasting into an email, instant message, Word document or any other file or text communication medium. Recipients decode the text by visiting the same website, pasting in the encrypted text, entering the password and selecting ‘decrypt’ before clicking the start button.
The software uses 256-bit AES encryption, which is considered by the US government to be suitable protection for information classified as ‘Top Secret’. The algorithm has never been cracked.
This launch follows January’s launch of Steganos LockNote, the company’s first freeware program which encrypts notes on the PC. Steganos LockNote looks like a normal text editor and works in the same way, with the small difference that it can only be opened using the correct password. Data entered into Steganos LockNote is automatically encrypted when the application is closed. Steganos LockNote is available to download at locknote.steganos.com .
Users visit www.steganos.com/freecrypt where there is a form into which they can type or paste text. They enter a password and click the button and their text is quickly encrypted and displayed in another form field. From there, it can be copied for pasting into an email, instant message, Word document or any other file or text communication medium. Recipients decode the text by visiting the same website, pasting in the encrypted text, entering the password and selecting ‘decrypt’ before clicking the start button.
The software uses 256-bit AES encryption, which is considered by the US government to be suitable protection for information classified as ‘Top Secret’. The algorithm has never been cracked.
This launch follows January’s launch of Steganos LockNote, the company’s first freeware program which encrypts notes on the PC. Steganos LockNote looks like a normal text editor and works in the same way, with the small difference that it can only be opened using the correct password. Data entered into Steganos LockNote is automatically encrypted when the application is closed. Steganos LockNote is available to download at locknote.steganos.com .
Wednesday, June 07, 2006
Skype as the attack vector
The most recent bug in Skype is another clue to enterprises that they should steer clear of the VoIP service, research firm Gartner recently warned. Two weeks ago, Skype patched a critical vulnerability that could let an attacker send a file to another user without his or her consent, and potentially obtain access to the recipient's computer and data.
Read the article HERE.
Read the article HERE.
University study tells why phishing works
Phishing works for so many reasons, we need to rethink browser and user interface design to provide some real-life security to the average user who doesn't see or understand the security cues.
Researchers at Harvard University and UC Berkeley have published a document explaining why phishing works on general users.
The ten-page document (PDF) details a small study of 22 participants that looks at today's standard security indicators used with websites.
Think that cues in the browser will help? Forget it.
Read the article HERE.
Researchers at Harvard University and UC Berkeley have published a document explaining why phishing works on general users.
The ten-page document (PDF) details a small study of 22 participants that looks at today's standard security indicators used with websites.
Think that cues in the browser will help? Forget it.
Read the article HERE.
Tuesday, June 06, 2006
ZoneAlarm Updated
While not a full-point upgrade, version 6.5 of the ZoneAlarm Internet Security Suite, released today, includes some significant advances. Most notable is the inauguration of a new online Identity Protection Center to help users avoid or recover from identity theft.
CNET has a detailed review HERE. PC Mag also has a review HERE.
CNET has a detailed review HERE. PC Mag also has a review HERE.
Monday, June 05, 2006
I forgot the administrator's password?
Ok, so you say you forgot your Windows administrator's password? How can you get out of this situation without formatting and re-installing the operating system?
Read the article HERE.
Read the article HERE.
Sunday, June 04, 2006
Essiantal Software : Comodo Personal Firewall 2.0
This firewall has been on my "Essential Software" list for some time. Comodo Personal Firewall is a kick-ass free firewall. It keeps hackers out and tricky unauthorized programs off the Internet. And it resists being terminated. It works as well as all but the best for-pay firewalls—and did I mention it's free?
"Comodo Personal Firewall offers truly excellent protection, on a par with the better for-pay personal firewalls. If you don't have firewall protection, your system is a train wreck waiting to happen—install Comodo now!"
PC Magazine has a full review [ including Screenshots ] HERE.
"Comodo Personal Firewall offers truly excellent protection, on a par with the better for-pay personal firewalls. If you don't have firewall protection, your system is a train wreck waiting to happen—install Comodo now!"
PC Magazine has a full review [ including Screenshots ] HERE.
Microsoft probes Windows DoS flaw
Microsoft is looking into a report of a Windows flaw that could cause certain applications to crash, the software maker said Thursday.
The potential flaw affects Windows XP and Windows Server 2003, Microsoft said in a statement. The bug could cause certain applications, including Internet Explorer, to crash after a user is tricked to click on an overly long Web link, security monitoring company Secunia said in an alert.
Full details HERE.
The potential flaw affects Windows XP and Windows Server 2003, Microsoft said in a statement. The bug could cause certain applications, including Internet Explorer, to crash after a user is tricked to click on an overly long Web link, security monitoring company Secunia said in an alert.
Full details HERE.
Saturday, June 03, 2006
Essiantal Software : CCleaner
Those of you that are using this programme are aware an update is available. Those of you that are not may like to try this excellent utility.
CCleaner (Crap Cleaner) is a freeware system optimization and privacy tool. It removes unused and temporary files from your system - allowing Windows to run faster, more efficiently and giving you more hard disk space. The best part is that it's fast! (normally taking less that a second to run) and Free.
Download HERE.
CCleaner (Crap Cleaner) is a freeware system optimization and privacy tool. It removes unused and temporary files from your system - allowing Windows to run faster, more efficiently and giving you more hard disk space. The best part is that it's fast! (normally taking less that a second to run) and Free.
Download HERE.
Get full service for your PC
Microsoft has fitted an anti-virus and PC clean-up utility into the new Windows Live initiative as part of a larger plan to shuttle customers to its Internet security offerings.
A beta version of the new Safety Center lets customers run free Web-based computer scans to detect and remove viruses and other known malware.
The Safety Center, which currently works only on the Internet Explorer browser, uses an ActiveX Control to scan for and remove viruses. It is also capable of detecting vulnerabilities on Internet connections.
Visit the Safety Center HERE.
A beta version of the new Safety Center lets customers run free Web-based computer scans to detect and remove viruses and other known malware.
The Safety Center, which currently works only on the Internet Explorer browser, uses an ActiveX Control to scan for and remove viruses. It is also capable of detecting vulnerabilities on Internet connections.
Visit the Safety Center HERE.
New Firefox Version Fixes 13 Security Holes
Mozilla on Thursday released a new version of its Firefox Web browser to correct 13 security holes, including at least five that Mozilla said could let attackers install software without any action on the part of the user.
If the security updates alone won't get you to switch, consider that the newer version of Firefox automatically applies patches when they are ready.
Read the article HERE.
If the security updates alone won't get you to switch, consider that the newer version of Firefox automatically applies patches when they are ready.
Read the article HERE.
Friday, June 02, 2006
20 Things You Won't Like About Vista
Computerworld's Scot Finnie details 20 things you won't like in Windows Vista, with a visual tour to prove it. He says that MS has favored security over end-user productivity, making the user feel like a rat caught in a maze.
"In its supreme state of being, Microsoft knows precisely what's best for you. It wants to teach you about what's best. It wants to make it harder for you to make a mistake."
Read the [13 page] article HERE.
"In its supreme state of being, Microsoft knows precisely what's best for you. It wants to teach you about what's best. It wants to make it harder for you to make a mistake."
Read the [13 page] article HERE.
Extortion virus code cracked
Do not panic if your data is hidden by virus writers demanding a ransom.
Poor programming has allowed anti-virus companies to discover the password to retrieve the hijacked data inside a virus that has claimed at least one UK victim.
The Archiveus virus caught out British nurse Helen Barrow and swapped her data with a password-protected file. The virus is the latest example of so-called "ransomware" that tries to extort cash from victims.
The 30-digit password locking the files is "mf2lro8sw03ufvnsq034jfowr18f3cszc20vmw". Using the password should restore all the hijacked files.
Read the article HERE.
Poor programming has allowed anti-virus companies to discover the password to retrieve the hijacked data inside a virus that has claimed at least one UK victim.
The Archiveus virus caught out British nurse Helen Barrow and swapped her data with a password-protected file. The virus is the latest example of so-called "ransomware" that tries to extort cash from victims.
The 30-digit password locking the files is "mf2lro8sw03ufvnsq034jfowr18f3cszc20vmw". Using the password should restore all the hijacked files.
Read the article HERE.
Thursday, June 01, 2006
Spyware tricks of the trade
I often hear questions asked about why do spyware pushers trash machines with their large bundles of garbage-ware and how do they do it.
The answer to why? is simple. It's always about the M O N E Y.
Read the article HERE.
New Ways To Fight Spyware and Spam
Thanks to spam and spyware, no one could blame you if you dread logging on to your computer these days. Too often it seems that you're either ridding your inbox of piles of unrequested, irrelevant e-mail messages or worrying about whether the latest computer slowdown is the result of some malicious software that's integrated itself onto your system.
If you're fed up, you have plenty of company.
Read the article HERE.
The answer to why? is simple. It's always about the M O N E Y.
Read the article HERE.
New Ways To Fight Spyware and Spam
Thanks to spam and spyware, no one could blame you if you dread logging on to your computer these days. Too often it seems that you're either ridding your inbox of piles of unrequested, irrelevant e-mail messages or worrying about whether the latest computer slowdown is the result of some malicious software that's integrated itself onto your system.
If you're fed up, you have plenty of company.
Read the article HERE.
